With all the talk of enhanced pat-downs/sexual assault/gate rape being conducted by the TSA at US airports (in the event that you wish to opt-out of the full body scan), I was wondering what the Canadian Air Transport Security Agency’s policy might be. Typically we seem to follow US rules fairly closely up here.
CATSA’s web page describing the full body scanning process does not even mention the option to opt-out. Their “Physical Search” page states the following:
A physical search may involve a Screening Officer using a wanding technique with a device that detects metal objects. During a physical search, a Screening Officer performs a visual search and a search through touch to ensure that a traveller is not concealing anything under his or her clothing.
Sounds pretty benign.
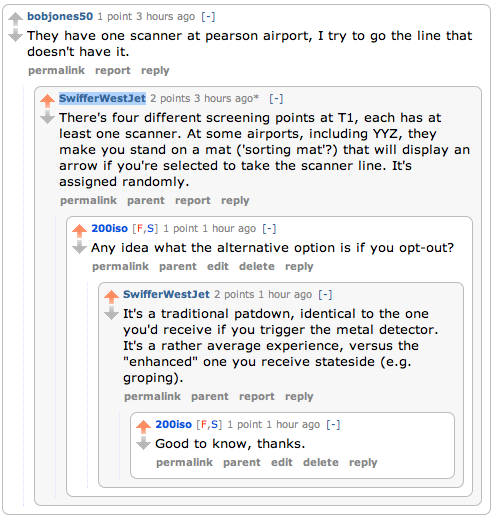
So I thought I’d ask Reddit for their experiences. A user named SwifferWestJet who seemed to know what they’re talking left a helpful comment. Essentially, the pat downs are “traditional.”